This guide is expected to help other people in the business who have started or improved their own product security programs and empower the business’s wide selection of crucial secure improvement strategies.
At SoftKraft we cover every component of SDLC - from security engineering and security operations to compliance operations and security automation. Fill the gaps between IT and security with our DevSecOps Consulting Services while ensuring safe and quick delivery of code releases.
Most organizations have a well-organized ensemble set up when it comes to creating, delivering, and maintaining real life programming projects. In any case, not in terms of obtaining that item. Multiple companies consider security to be a stumbling block—something that causes them to try to change and prevents them from getting new options to get along with.
Regardless, programming with no proper planning puts organizations in danger. Advanced features will not help you or your customers if your project has exploitable flaws that skilled engineers can exploit.
Your organization must integrate security into the entire Software Development Life Cycle (SDLC), allowing, rather than restricting, the delivery of incomparable evaluation, significantly secure items to the market.
Security can be a big part of any application that includes a lot of useful features. This could be as straightforward as protecting your knowledge base from malicious actors, or as complex as encapsulating all the transaction happing between two end point within your product or in an organization.
Security should be at the forefront of your designers' minds as they work on your requirements, assisting you in detecting problems in necessities earlier than they manifest as security issues in progress. An instant setup provides a coordinated approach to managing application security. There has been a lot of progress in terms of best practices for ensuring security and consistency. These practices should be incorporated into all phases of programming development and support for a variety of noteworthy advantages.
What is the Secure Development Lifecycle (SDL)?
A software development lifestyles cycle (SDLC) is a strategy for the manner towards constructing an utility from starting to decommissioning. Throughout the lengthy term, several SDLC fashions have arisen—from the cascade and iterative to, even more as of late, light-footed, and CI/CD, which hastens and recurrence of sending.
As a rule, SDLCs incorporate the accompanying stages:
- Planning and requirements
- Architecture and design
- Test planning
- Coding
- Testing and results
- Release and maintenance
Secure SDLC is a set of best practices aimed at making the standard SDLC more secure. Making a secure SDLC measure necessitates focused effort at each stage of the SDLC, from requirement gathering to planning and maintenance. Secure SDLC necessitates a mental shift among the development team, focusing on protection at every stage of the project rather than just at the end. This lessens the danger of discovering security weaknesses in your application and attempts to limit the effect when they are found.
Designers presently should be cognisant of potential security worries at each progression of the cycle. This requires incorporating security into your SDLC in manners that were not required previously. As anybody can conceivably access your source code, you need to guarantee that your code is hard to crack. In that capacity, having a hearty and secure SDLC measure is basic to guaranteeing your application is not liable to assaults by programmers and other detestable clients.
Secure SDLC's point is not to totally dispense with conventional security checks. Before, associations typically performed security-related exercises just as a component of testing—toward the finish of the SDLC. Because of this late procedure, they would not discover bugs, defects, and different weaknesses until they were undeniably more costly and tedious to fix. The assets detailed that it cost multiple times more to fix a bug found during execution than one recognized during plan.
Many secure SDLC models are being used, however outstanding amongst other known is the Microsoft Security Advancement Lifecycle (MS SDL), which depicts 12 practices associations that can embrace to expand the security of their product. Furthermore, recently, NIST distributed the last form of its Protected Programming Improvement System, which centres around security-related cycles that associations can incorporate into their current SDLC.
What are the benefits of SDL?
Secure SDLC is a definitive illustration of what is known as a "shift-left" drive, which alludes to incorporating security checks as right off the bat in the SDLC as could really be expected.
Doing so, helps advancement groups appropriately plan discharges, making it simpler to catch and address gives that emerge that could influence the delivery timetable. This is unquestionably desirable over getting an undesirable astonishment once the application sends to creation. SSDLC, in this manner, helps keep discharges on target.
SSDLC at its centre has the security endeavours being driven by the advancement group itself. This permits the issues to be fixed by the area specialists who composed the product as opposed to having an alternate group fix the bugs as a bit of hindsight. While the extra effort of safety testing within the SDLC interaction may appear to be a lot of work and expensive to put together, the vast majority of it is now being robotized.This is especially valid for advancement tasks or DevOps (more on this as follows).
The safe SDLC requires cooperation among DevOps and the specialists executing the application's usefulness, and this joint effort should be fused into the SDLC itself. By fixing these issues from the get-go all the while, advancement groups can decrease the absolute expense of responsibility for applications.
Finding issues late in the SDLC can bring about a 100-overlap expansion in the advancement cost expected to fix those issues, as found in the outline beneath. There are endless benefits of utilizing a protected programming advancement life cycle. Here are a portion of the best ones that you should think about.
Early detection of vulnerability flaws saves you time and money Production software fixes are significantly more expensive as compared to constantly attending to the problem during the SDLC.

Security decisions are coordinated right from the planning stage Both the management and the development team are aware of the project's security risks and concerns. As a result, the development framework can be tweaked as the SDLC progresses to ensure stable code is generated.
Secure SDLC creates security culture that limits business risks Organizations that fall victim to online security attacks lose far more than they think, whether it's daily security attacks like SQL or XML injections, or simple security issues like DoS (denial of service).
SSDLC likewise gives an assortment of side advantages, for example,
- Improvement groups get persistent preparing in secure coding rehearses.
- Security approaches become more reliable across groups.
- Clients have more faith in you because they see how much attention you pay to their safety.
- Interior security improves when SDL is applied to in-house programming apparatuses.
Information leaks can have a negative impact on a company's reputation, stock value, client relations, client consistency levels, and deals. A secure SDLC protects an organization from a few cyberattacks by preventing most security flaws in a convenient manner.
Secure software development in practice
Before we talk about how to add SDL practices to programming improvement, we should think about common advancement work processes. The least difficult cascade work process is direct, with one phase coming after the other:
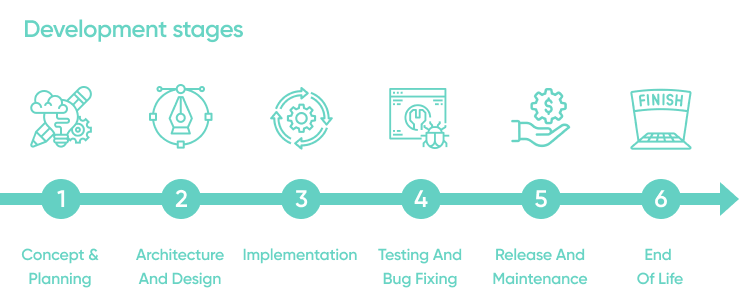
Secure SDLC process has an impact on each stage of the product development process. It requires an outlook that is centred around secure conveyance, bringing issues up in the necessities and improvement stages as they are found. This is undeniably more productive—and a lot less expensive than sitting tight for these security issues to show in the sent application. Secure programming improvement life cycle measures fuse security as a segment of each period of the SDLC.
While incorporating security into each period of the SDLC is most importantly an outlook that everybody needs to bring to the table, security contemplations and related assignments will really fluctuate essentially by SDLC stage.
Commonly, secure programming improvement lifecycle measures are separated into the accompanying stages:
Concept and planning
The reason for this stage is to characterize the application idea and assess its suitability. This incorporates building up a task plan, composing project necessities, and designating HR.
Secure development lifecycle rehearses suggested for this stage include:
Secure design principles Security design begins with setting security targets. At that point, select an SDL procedure and compose an itemized plan of applicable SDL exercises. This guarantees that your group will address security issues as ahead of schedule as could really be expected.
Security considerations Set up a rundown of safety prerequisites for your secure software. Make sure to incorporate both specialized and administrative prerequisites. Having this rundown serves to handily recognize and fix conceivably rebellious spaces of your undertaking.
Security awareness sessions Security training should cover a wide range of security topics, from basic threat awareness to inside and out information on safe outcomes. Furthermore, fundamental security training instills a sense of security in all task members and secure plan standards are demonstrated to key task members in advanced courses.
Receiving these practices improves the accomplishment of task arranging and secures application consistence with security principles. This stage additionally distributes the important HR with skill in application security.
Architecture and design
The reason for this stage is to plan an item that meets the prerequisites. This incorporates demonstrating the application construction and its utilization situations, just as picking outsider parts that can accelerate improvement. The aftereffect of this stage is a plan report.
Security development lifecycle rehearses suggested for this stage include:
- Threat modelling Danger demonstrating comprises of recognizing likely assault situations and adding significant countermeasures to the application plan. Demonstrating uncovers potential dangers early, accordingly, lessening the related expenses, and furthermore lays the reason for future episode reaction plans.
- Secure design The plan report and ensuing updates are approved considering the security prerequisites. Early plan surveys help with distinguishing highlights presented to security hazards before they are carried out.
- Third-party software tracking Weaknesses in third-party components can weaken the entire system, so it's critical to monitor their security and apply patches as needed. Outsider programming checks are used to identify regions that have been weakened by depleted segments and to fill in the gaps.
Receiving these practices identifies flaws before they make their way into the application. Checking consistence mitigates security chances and limits the opportunity of weaknesses beginning from outsider segments.
Implementation
This is the stage at which an application is really made. This incorporates composing the application code, troubleshooting it, and delivering stable forms reasonable for testing.
Secure software development rehearses suggested for this stage include:
Secure coding Aides and agendas help software engineers to remember average slip-ups to be kept away from, for example, putting away decoded passwords. Implementing secure coding standards disposes of numerous minor weaknesses and saves time for other significant errands.
Static scanning Static application checking devices (SAST) survey recently composed code and discover likely shortcomings without running the application. Day by day utilization of static examining apparatuses uncovers botches before they can advance into application assembles.
Code review Automated and manual code audits are yet an indubitable requirement for building secure applications. Convenient surveys assist designers with hailing and fix likely issues before they shift thoughtfulness regarding different undertakings.
Receiving these practices decreases the quantity of safety issues. Consolidating programmed checking and manual surveys gives the best outcomes.
Testing and bug fixing
The reason for this stage is to find and address application mistakes. This incorporates running programmed and manual tests, distinguishing issues, and fixing them.
Secure software development lifecycle rehearses suggested for this stage include:
- Dynamic scanning Dynamic application scanner instruments (DAST) uncover weaknesses by reproducing programmer assaults at runtime. To lessen bogus positives, you can utilize a joined methodology (IAST).This method includes observing the executed code and application information stream in addition to runtime checking. As well as finding normal weaknesses, dynamic checking pinpoints setup blunders that sway security.
- Fuzzing Fluff testing includes creating arbitrary sources of info dependent on custom examples as well as examining if the application can deal with such data sources appropriately. Robotized fluffing devices improve assurance from assaults that utilization contorted data sources, like SQL infusion.
- Penetration testing It is a smart thought to welcome an outsider group of safety experts to re-enact potential assaults. Outer specialists depend on their insight and instinct to recreate assault situations that may be neglected by your group.
Receiving these practices decreases the number of safety concerns much more. In combination with the exercises from preceding stages, this provides good protection against a large collection of the known dangers.
Release and maintenance
At this point, an application goes live, with numerous examples running in an assortment of conditions. In the end, new forms and fixes become accessible and a few clients decide to redesign, while others choose to keep the more established variants.
Secure SDLC rehearses suggested for this stage include:
Environment management Genuine aggressors misuse climate design mistakes and weaknesses. Security observing should cover the whole framework, not simply the application. Such observing enhances the general security of your application.
Incident response plan An episode reaction plan clearly depicts the methodology that your occurrence group should use to deal with any security breaches that may occur. Quick execution of the reaction plan is pivotal for emergency and fix of safety breaks. Check our Incident response plan article for more details.
Ongoing security checks Security checks should be rehashed consistently for the reason that new sorts of weaknesses are being found at a consistent rate. Standard checks shield your application from newfound weaknesses.
Receiving these practices assists with reacting to arising dangers rapidly and adequately.
End of life
"End of life" refers to the point at which a product's Developer no longer supports it. Applications that store delicate information might be dependent upon explicit finish of-life guidelines.
Secure SDLC exercises suggested for this stage include:
- Data retention For some types of information, governments define maintenance strategies. The risk of unexpected fines is reduced by double-checking your organization's maintenance arrangements for compliance with legal requirements.
- Data disposal When an application reaches the end of its life cycle, all sensitive data stored in it should be cleansed carefully. Encryption keys and individual data are examples of such information. Legitimate data removal near the end of life maintains such information private and protects against data breaches
By receiving these practices, designers guarantee sufficient opportunity to create strategies that consent to unofficial laws.
Consider before starting a secure SDLC?
Here are some things you can do as a developer or tester to move toward a secure SDLC and improve your organization's security:
Set security standards
Focus on educating yourself or even your coworkers about the finest secure coding strategies and security frameworks:
- Establish secure coding rules.
- Make designers aware of security best practices.
- Setting clear expectations for intended SLA.
Not these need to occur for a successful secure SDLC execution, yet similar as a jigsaw puzzle, you will need to assemble enough pieces before you can see the higher perspective.
Collect requirements clearly
Whatever you make, it ought to be straightforward. Advancement groups need clear necessities that are not difficult to follow up on. This applies to all security exhortation, suggestions, and rules. Any weaknesses found in tests should be not difficult to follow up on.It's critical that everyone involved, including individuals, cycles, and instruments, bring solutions to the table rather than simply drawing attention to problems.
Build secure development culture
Since secure SDLC will change how various groups function and interface, it is significant for everybody to go into this involvement in a receptive outlook, and for the security group to have the attitude of engaging engineers to get their own applications.

For grounded applications and groups, it might regularly be simpler to execute secure SDLC changes when it is attached to another modernization exertion, like a cloud change, a DevOps drive, or its greater security-cognizant variety, DevSecOps.
Tackle the major issues first
Instead of focusing on each flaw discovered, concentrate on the most important issues and noteworthy fixes. While it could be feasible for fresher or more modest applications to fix each security issue that exists, this will not really work in more seasoned and bigger applications. An emergency approach can likewise be useful. This focuses on not only preventing security flaws from making it into production, but also ensuring that existing flaws are triaged and addressed over time.
Perform an Architectural Risk Analysis
The design hazard examination measure incorporates ID and assessment of dangers and hazard effects and suggestion of hazard diminishing measures. Configuration imperfections represent half of safety issues. You cannot discover configuration deserts by gazing at code—a more significant level agreement is required. That is the reason architectural risk analysis serves a fundamental part in any strong programming security program.
Conclusion
Understanding the six stages of the SDLC and their security perspective is critical in light of the growing demand for more smoothed out and manageable advancement models with secure structures.
A SDLC is methodological, guaranteeing that you, your association, and its elaborate partners plan, make, and send a result in an ideal and automatically effective way.
In any case, making the privilege SDLC requires the best designers you can get your hands on. Therefore, you need to employ qualified and dependable engineers that ensure the quality and trustworthiness of your undertakings.

![Secure Software Development Lifecycle [Practical Guide]](/.netlify/images?url=_astro%2Fsecure-software-development-lifecycle-v5.D0wUrAv4.png)