As cyber risks and attacks continue to grow, the importance of security orchestration throughout an application's life cycle has become critical. The average cost of a single corporate data breach in 2020 was $8.64 million, or $150 per breached record, according to a Digital Guardian study.
DevSecOps is gaining traction in the industry today. According to a recent study conducted by IDC, the global pandemic has accelerated the adoption of DevOps and DevSecOps practices, resulting in increased demand for new services and application usage. As a result, nearly 75% of all businesses have accelerated their DevSecOps efforts.
Knowing the answer to the question "what is DevSecOps methodology" and why DevSecOps practices are critical can assist you in taking the appropriate steps to protect your organization from security risks.
What is DevSecOps?
DevSecOps is the practice of integrating security into the software delivery model that combines project management workflows with automated IT tools. Its foundation is a culture in which development and operations are empowered to share responsibility for delivering secure software through processes and tooling.
The term DevSecOps first appeared in a January 2012 blog post by Neil MacDonald of Gartner, who suggested that the DevOps vision was "incomplete without the incorporation of information security, which represents yet another silo in IT.”
DevSecOps vs DevOps
At a fundamental level, the distinction between DevOps and DevSecOps would be one of integration — while many DevOps methodologies incorporate security teams into the process, DevSecOps places a dedicated emphasis on introducing security earlier into the software development lifecycle, beginning with the requirement stage, and to deliver secure software faster.
Security tooling is injected early in the process, rather than adding security controls after the product is released. This is accomplished by introducing application security testing early in the development and making security teams part of the development teams, rather than a separate team.
This enables scalability while also fostering a shared responsibility culture that brings security into alignment with DevOps culture. The approach helps minimize vulnerabilities that reach the production environment, therefore lowering the cost of resolving application security issues.
Security in every stage of the DevOps process:
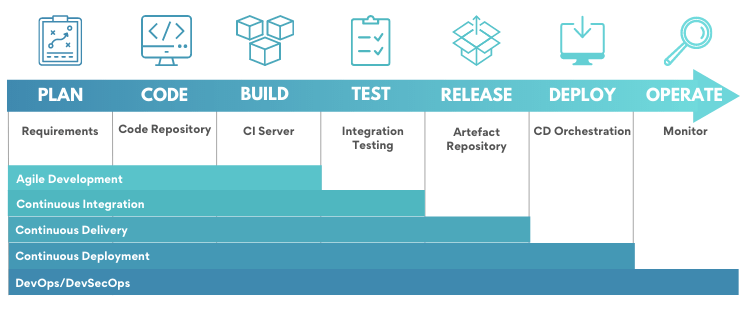
Benefits of DevSecOps
Without DevSecOps, by the time operations teams conduct security checks, the products will have passed through the majority of the other stages and will be nearly complete. As a result, detecting a security threat at such a late stage required rewriting countless lines of code, an agonizingly time-consuming and laborious task.
Better collaboration between development security and operation provides multiple advantages over the long run:
Costs reduction. By identifying vulnerabilities early in the SDLC cycle, you can significantly reduce the costs associated with resolving them. Multiple teams collaborating on security increases accountability. Additionally, collaboration enables the development of rapid and effective security response strategies and more robust security design patterns.
Compliance. DevSecOps practices are critical for adhering to industry-standard regulations. Regulations such as the General Data Protection Regulation (GDPR) require extreme caution when it comes to data handling. DevSecOps provides managers with a holistic view of such measures, creating a more conducive environment for compliance.
Observability. A holistic view of an organization's infrastructure security enables teams to monitor everything from infrastructure to customer-facing applications and supporting services. You can take it a step further by utilizing AI and machine learning tools to monitor availability, performance, and diagnose problems in advance of their impact on customers and the business.
Traceability. DevSecOps tools enable teams to detect and react to security issues faster on the ever-growing number of cloud applications and services.
How do you implement DevSecOps?
DevSecOps process implement is not created by simply putting together development, operations, and security team members.
Many different DevSecOps structures approaches exist, ranging from relatively siloed designs where all three sides work independently to fully integrated operations where duties are freely shared among team members:
Shift-left - bake security from the beginning
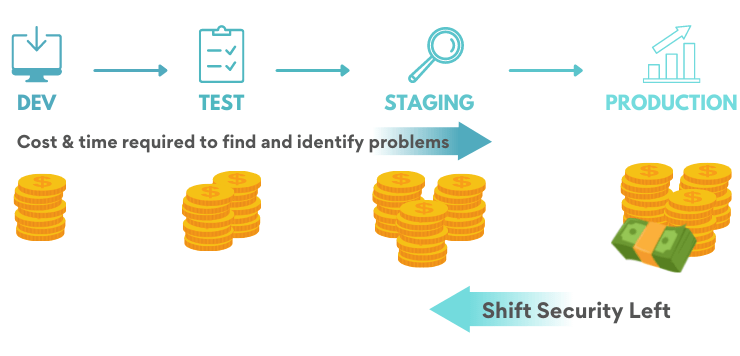
Shift-left testing entails building security controls into your applications from the start, rather than waiting until the end of the delivery chain to test application security:
Make security part of planning. Feature-based descriptions alone will not suffice. Define security acceptance test criteria and threat models for known vulnerabilities.
Embrace DevOps workflow. If your software development teams have not yet implemented the CI/CD pipeline, your first step should be to do so. Introduce a shorter development cycles and more frequent deployments.
Align and integrate security with your DevOps workflow. The goal is to integrate secure code practices and security tools directly into the development process, including automated security testing.
Embrace automated DevSecOps tools. Adding additional security tests naturally slows down the development pipeline, which may cause frustration among your development team. Keeping as much as possible automated will help maintain a high level of throughput.
Implement application monitoring tools. When code has been deployed, you must maintain integration of security. When vulnerabilities are identified, security teams must be prepared to implement remediation procedures.
Security activities as part of DevOps process:
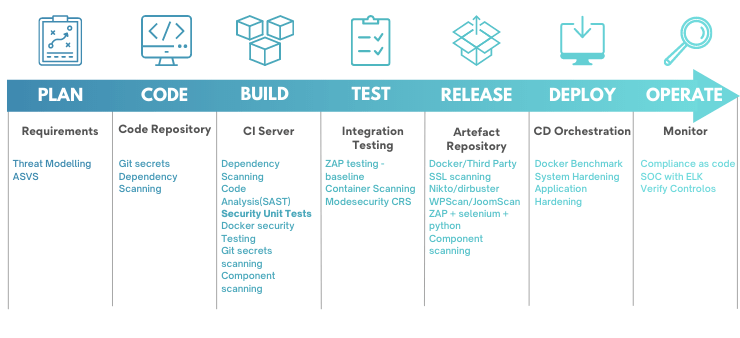
The obvious benefit of this approach is that you can quickly identify vulnerabilities and work on resolving them. Additionally, the sooner you apply security testing to discover security threats, the less expensive it will be to address them.
Secure by default
With passwords left on public GitHub repositories, even the laziest hacker could gain access to your cloud applications. Moreover, with the privileged credentials they've acquired, they could hop from resource to resource across your network, potentially gaining access to sensitive data. That’s why security decisions need to be part of the software development process from the start:
Implement Password Management. Storing IDs and passwords in plain text within code carries significant risk. Application-to-Application Password Management (AAPM) completely eliminates hard-coded credentials. A digital password vault securely stores credentials and provides multi-layer security through automated verification procedures, ensuring that authentication is quick and DevOps production runs smoothly.
Monitor privileged access to ensure accountability. Monitor all privileged user access to files and databases, audit new user creation and privilege grants, and restrict the use of shared-privileged accounts.
Facilitate end-to-end data encryption. End-to-end encryption is the most secure method of transferring confidential data at the moment, which is why an increasing number of communication services are adopting it.
DevSecOps Maturity Model (DSOMM)
From startups to multinational corporations, software development is dominated by Agile framework and product teams. Security problems are frequently overlooked or are taken into account insufficiently during the initial design and in the delivery process.
The OWASP DevSecOps Maturity Model provides opportunities to harden your software development and shows what should be prioritized.
Static Depth: How deep is static code analysis?
Dynamic Depth: How deep are dynamic scans executed?
Intensity: How intense are the majority of the executed attacks?
Consolidation: How complete is the process of handling findings?
Learn more: DevSecOps Maturity Model
Security Tools in CI/CD
Automating security comes in a variety of forms and sizes. Traditional security scanners and policies can be programmed to check for set security vulnerabilities. Scans can be triggered automatically or manually in response to check source code commits for security vulnerabilities. Their result in automated remediation and reports or require human intervention.
Here are some tips for implementing security testing key performance indicators into your software development practices:
Everything as Code (EaC). Auditable, measurable, and secure.
Anything which takes more than 10 minutes (me being optimistic), isn’t fit for CI/CD. See if your tools provide incremental/baseline scans.
SAST/DAST without creating custom rules/tweaks is of not huge benefit down the line.
Fail security tests need to create separate tasks for easier debugging. Link wiki in the scan outputs if someone needs some answers.
Security tools for our Python development services:
| Security Test | Python Tool |
| SAST | Bandit |
| DAST | ZAP Baseline |
| Hardening | Ansible |
| Compliance | Inspec |
| Git Secrets | Trufflehog |
People, Process, and Technology
The holy trinity of people, process, and technology is critical to DevSecOps success:
People. Your development team is unlikely to be security professionals, and even if they are not the first line of defense, it is critical to educate them. DevSecOps is most effective when everyone understands and adheres to security principles and requirements.
Process. DevOps and Agile frameworks are based on the concept of establishing a collaborative, shared responsibility that is constantly improving. Development organizations need the integration of security into DevOps workflow to build secure code.
Technology. Equip your development security and operations teams with the security tooling necessary to execute security controls effectively. Include automation and configuration management, Infrastructure as Code, automated code scans, host hardening, monitoring, etc.

Challenges of DevSecOps implementation
As with any new methodology, DevSecOps can be challenging to implement and sustain over time. Some of the biggest obstacles are as follows:
Security is inherently poorly understood: Many developers lack an understanding of security threats and best practices, making it difficult to integrate laser-like focus consulting services into the development cycle.
Security practices affect the Agile delivery cycles. Security testing frequently clashes with the Agile rapid release cycles. This drives the need to use security automation tools in DevSecOps environments to deliver secure software faster.
New tools to be adopted and learned. DevSecOps adopters will find that they must ask staff to work with new people and development processes. Similarly, security professionals will have to master development-centric tools.
How to build DevSecOps culture that lasts?
To ensure long-term success, it's critical to focus on developing a culture that supports your DevSecOps team members.
Show leadership support for DevSecOps. If management does not demonstrate a strong commitment to security, there is little chance that the rest of the organization will. Without a clear mandate from the CTO down, it will be nearly impossible to cultivate a culture that takes security seriously.
Build shared responsibility culture. The most common DevSecOps reasons for failure are team members’ conflicts and departmental silos. Reward openness, flexible collaboration, and knowledge sharing, which promotes continuous improvement.
Invest in education. Start with providing security training to developers while also assessing what skills you need with DevSecOps consulting services. Your goal needs to be to implement an effective DevSecOps environment with minimal effort.
Conclusion
Historically, application security was frequently an afterthought. However, bypassing or trivializing security is a risky strategy that could have far-reaching consequences once the app is deployed.
DevSecOps is focused on ensuring security throughout the development process. DevOps teams must automate security to safeguard not only the development environment and data but also the continuous integration and delivery process.
Security automation during the development cycle mitigates the risk of errors and misadministration, which could result in production attacks or downtime. DevSecOps implementation has a direct benefit, as it enables organizations to release code quickly but securely.



![AWS Security Incident Response Plan [Practical Guide]](/uploads/aws-security-incident-response-plan.png)
![Incident Response Plan Template For Startup [SM, MD, XL]](/uploads/incident-response-plan-template.png)